Introduction
Fraud is not a new problem -- but it's a growing problem, especially in IVR systems and contact centers where more advanced authentication and fraud prevention techniques have traditionally lagged behind other customer engagement channels such as websites and mobile applications.
Voice biometrics technology offers a powerful, undetectable defense that companies can implement in their contact center. Using intelligent AI responses from the IVR, live conversations with an agent, or existing session recordings, companies can apply voice biometrics to confirm the identity of the caller, compare questionable callers to one or more fraud databases, and evaluate the caller's speech to ensure that it is not a sophisticated AI (or "deepfake").
Voice biometrics, like fingerprints and iris scans are not 100% perfect. Some small amount of fraud may still slip through, and some amount of false positives may still occur. However, if a majority of the fraud is correctly detected in advance that would not be otherwise detected, the reduction of fraud losses can be dramatic.
Types of Contact Center Fraud
There are many potential forms of contact center fraud. For the purposes of this article, we will concentrate on a few that we are asked about the most:
-
Account Takeovers
-
Duplicate Registrations
-
Deepfakes
Account Takeover (ATO) Fraud
An account takeover occurs when fraudsters use stolen credentials, such as username and password, or social engineering, such as uncovering your knowledge-based authentication answers, to gain access to your account. IVR systems are susceptible if they employ simple questions to authenticate the caller. And call center agents can also be duped when fraudulent callers know personal questions, have access to account numbers, and even have access to your phone or devices. This is not uncommon as, for example, much bank fraud is considered "friendly fraud", often being committed by family or close friends. Significant losses can occur once your account is compromised.
Duplicate Registration Fraud
Duplication registration fraud is different from ATO fraud. In ATO fraud, the fraudster does not have a legitimate existing account. Duplicate registrations occur when a fraudster has already setup at least one account -- and is successful setting up another account. This type of fraud is more common in retail situations, where there are incentives for having multiple accounts with fake identities. For example, the telesales arm of a cellphone phone company could ship a new iPhone to an illegitimate account holder -- or multiple phones to different locations for the same fraudsters -- costing the company significant sums. The same holds true for almost any telesales organization.
Deepfake Fraud
Deepfake fraud is a more recent phenomenon, but a growing area of concern. In the speech technology world, "deepfake" technology is also referred to as "synthetic speech" or "voice cloning". The general concept is that powerful artificial intelligence (AI) algorithms can model your voice using from a few seconds to a minute or so of your speech. The technology has evolved in recent years to the point where it can very closely replicate your voice with great accuracy. This is NOT science fiction, but reality. See this article from 2019. Not only are huge losses possible, but now conversations that regularly occurred between callers and agents, where they "know" each other, may be called into question.
Key Voice Biometric Functions
Before diving into how the IngenID One™ Platform helps to specifically address these types of fraud, we'll review some of the key voice biometric functions that are used:
Enrollment
In voice biometrics, "enrollment" is the process where one or more speech samples are gathered, sent to a voice biometric engine, and are processed by sophisticated deep learning models to create a unique voiceprint. Voiceprints, sometimes also called models or templates, are then typically encryped and stored in a database.
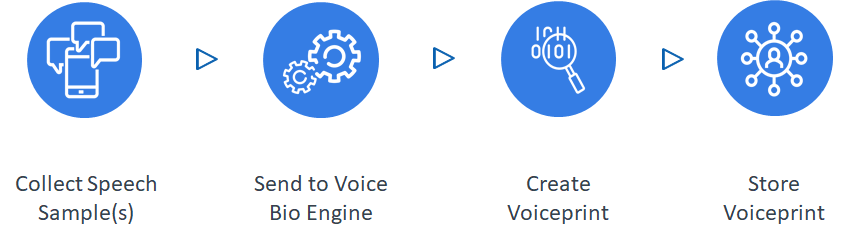
The use of voiceprints and various forms of matching is fundamental to the power of voice biometrics in fighting fraud in your contact center. The IngenID One™ Platform can be configured to create an unlimited number of voiceprint databases. For instance, we can set up a customer database for your true, validated customers. Then, we could set up one or more fraudster databases to contain voiceprints you create from fraudster speech samples. More on this later.
Verification
In voice biometrics, "verification" is the process where a user or caller makes a claim of identity. They then supply a speech sample. This speech sample is compared to the stored voiceprint for their claimed identity using a 1:1 matching process. Matches occur quickly and accurately.
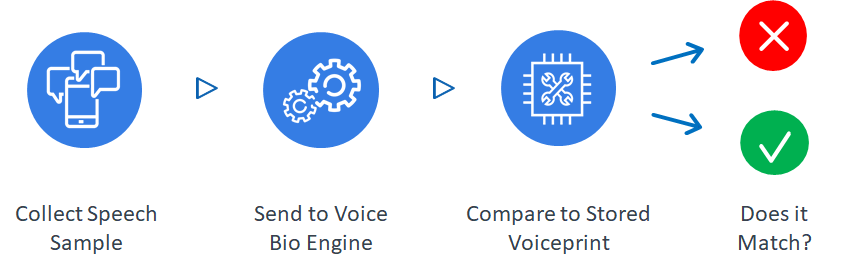
The use of the verification function in voice biometrics is a powerful weapon in the fight against fraud. This function is easily integrated into simple IVR systems, advanced IVRs or intelligent or converational AIs, and also real-time conversations between caller and agent. A verification request is typically the first line of defense in your IVR or contact center. The resulting score is an indicator of confidence -- it will set the stage for potential follow-up actions.
Identification
In voice biometrics, "identification" is performed when you do not have a claim of identity -- or, the claim of identity is suspect. When identifying, a speech sample is compared to a database of stored voiceprints, or a subset of them, in order to determine if a likely match exists. This is a 1:N process that can be time-consuming depending on the number of voiceprints being evaluated.
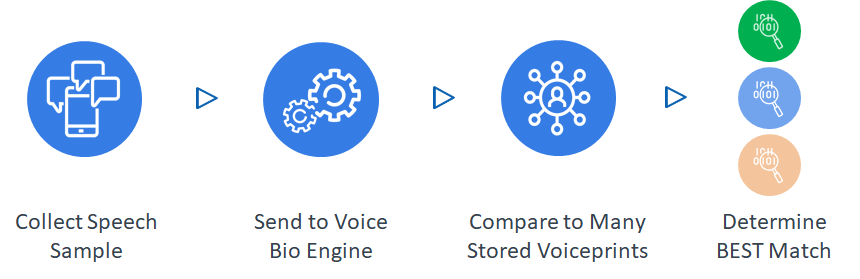
Identification is one of the key tools we use to address the first 2 types of fraud -- Account Takeovers and Duplicate Registrations.
Spoof Detection Algorithms
Relative to voice biometrics, "spoofing" refers to providing fraudulent speech in an attempt to pass it off as being spoken by the actual speaker in real time. This fraudulent speech can be created by sophisticated text-to-speech (TTS) or voice synthesis algorithms, by using existing recordings directly (i.e., a recorded playback attack), by using speech recordings that have been morphed or converted (i.e., speech conversion), or perhaps by a skilled mimic.
In The News good. For example, read about Microsoft's VALL-E. Obviously, there are some pretty scary implications to having a tool like this widely available.
IngenID, like many other voice biometrics companies, has developed spoof detection algorithms. We've also developed our own speech synthesis tools. Consider the two samples below. One is the actual real speaker, while the other one is synthetic speech (i.e., a deepfake). Can you tell the difference?
It really is difficult to tell the difference -- and we aren't going to say which is which. Suffice it to say, our spoof detection algorithms know the difference!
Detecting Fraud with the IngenID One™ Platform
Not every IngenID client will need all of our anti-fraud tools. Fraudsters are typically motivated by financial gains, and fraudsters typically seek the path of least resistance. IngenID is able to custom configure our platform to each client's unique needs, allowing for the most efficient and cost-effective deployment of our technology. Below are examples of common configurations:
Detecting Account Takeover (ATO) Fraud
Account takeover applies to many situations; it is not limited to call centers or IVR systems -- any contact channel is subject to takeovers. For contact channels involving voice, the IngenID One™ Platform can be set up to perform mutltiple steps:
-
Verification - multiple failed verification scores can indicate ATO activity. We have monitoring that can detect X failures during Y time period and can automatically lock the account.
-
Identification - multiple failed verification samples can be compared to one or more fraudster databases to determine if a known fraudster is at work. New fraudsters can also be added to fraudster databases.
-
Alerting - any cases where multiple failures lead to account locks, and/or fraudsters are identified, will trigger alerts to monitoring consoles, email distribution lists, etc.
Detecting Duplicate Registration Fraud
Registration means "enrollment", or creating a voiceprint. For certain industries and scenarios, end customers may be motivated to re-register as someone else, often to receive free or discounted merchandise or special "new customer" terms. This is a fairly straightforward issue to address:
-
Enrollment + Identification - during enrollment, speech samples are compared to voiceprints for any appropriate end customers using the Identification function. If a strong match is found, the identity is flagged for further investigation.
-
Assessment - Flagged identities can be reviewed by a fraud team member. A verified case of a duplicate registration attempt then triggers a move of the customer identity from the "real customer" database to the "fraudster" database and the existing registration request cancelled (and any pending transactions/activities).
Detecting Deepfake Fraud
Deepfake fraud is on the rise and can potentially be found in every contact channel. From a voice biometric perspective, detecting deepfakes is a fundamental component of the IngenID One™ Platform. Unlike other competitors, IngenID does not charge extra for detecting deepfakes.
-
Sample Submission - every sample that is submitted to the IngenID One™ Platform, whether for enrollment or verification or identification, is evaluated with our synthetic speech detection engine. This is a fast process that runs in parallel to the normal operation of the platform.
-
Response Code - a specific response code is returned which allows the calling application to take an appropriate action. Monitoring consoles are also alerted and service logs are updated accordingly.
How Much Does It Cost?
IngenID does not have a per-use pricing model for our anti-fraud tools. Brute force attempts to takeover accounts, the use of recorded playback attacks, and the use of synthetic speech are all fundamental elements of the IngenID One™ Platform which are included in the base cost of our services.
The use of the identification function (1:N matching) and orchestration functions required to manage fraudster databases requires either a private hosted deployment or a premise deployment of the IngenID One™ Platform with the Anti-Fraud Tools add-on, and possibly the Streaming Media Adapter add-on (details here). The pricing for these approaches is our "hybrid" technique. You pay a fixed monthly fee (like a subscription) that allows for unlimited users and usage of the platform and add-ons. There are monthly tiers based on aggregate volume.
Get Started
If you are concerned about potential fraud, or have a business that is known to be susceptible to fraud, the next step is to contact IngenID. We can conduct some brief discovery to determine if our tools can be applied to your computing environment, whether any significant obstacles exist, whether there can be fraud cost savings and or solution ROI, etc.

